Key Management Architecture
FaceWallet is a non-custodial wallet, meaning that the user, not the wallet service provider, has the right to control the wallet.
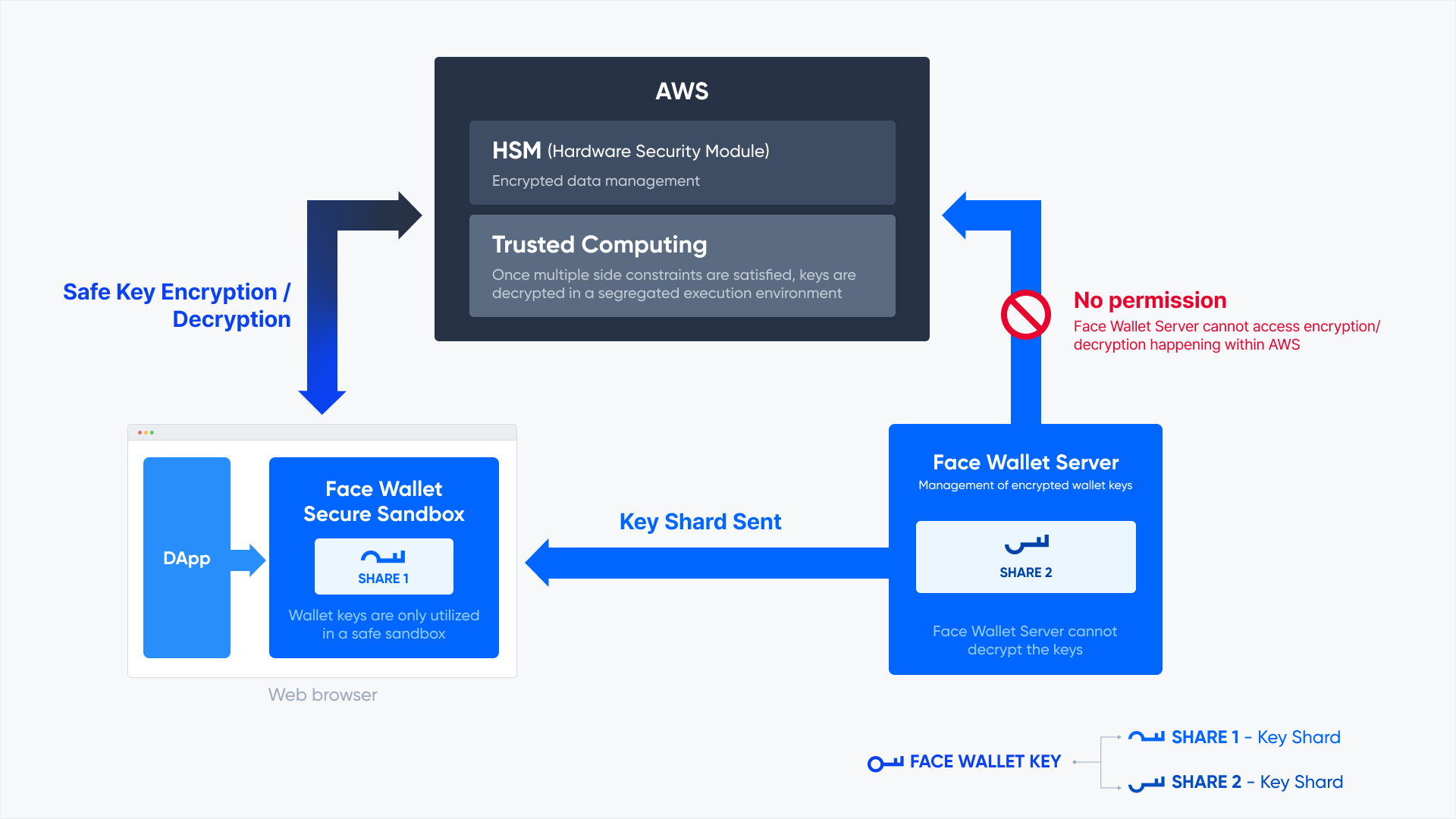
Who has the Key to the FaceWallet?
The Seed Phrase of FaceWallet is split into 2 shares. Share 1 is stored in a secure infrastructure environment and, usually, also in the user’s device. Share 2 is kept in the FaceWallet team's repository. Shares 1 and 2 are all securely encrypted and stored.
How is this made possible?
The infrastructure environment in which Share 1 is stored is encrypted using KMS applied with HSM. And the environment operates in a secure Trusted Computing environment that is not accessible by any one including the FaceWallet team and cannot be modified. In short, the FaceWallet team cannot figure out or obtain Share 1.
If the device has been used to log in at least once, Share 1 will be saved to the device in encrypted format. If Share 1 is deleted or logging in is made from a new device, Share 1 can be downloaded in a secure infrastructure environment through social login authentication.
Share 2 is stored encrypted in a secure environment controlled by the FaceWallet team. If a user successfully verifies the PIN code, the user can obtain Share 2.
Share 1 and Share 2 are decrypted securely in a Trusted Computing environment. You can sign transactions through the decrypted Seed Phrase, and sensitive data is immediately deleted upon signing.
Is it recoverable?
If a user forgets the PIN code or the PIN code is discarded because the user attempted with a wrong PIN code 5 times continuously, the PIN code can be reset through SMS OTP authentication. SMS OTP authentication must be performed with the mobile phone number that the user used to verify when the user created the wallet.
Updated about 1 month ago