[October 04, 2022] Change of Network Parameter, Supporting BNB Smart Chain and Klaytn, UI Support for ERC-1155 Type NFT Transfer
Face Wallet SDK version: v1.1
Hello. We are the Face Wallet team!
We inform you about the features and improvements newly added to Face Wallet on October 4, 2022.
Change of Ethereum/Polygon Network Parameter
The network parameter required to initialize an existing Face object has been changed.
Before change
| Blockchain | Mainnet Parameter | Testnet Parameter |
|---|---|---|
| Ethereum | Network.ETH_MAINNET | Network.ETH_TESTNET |
| Polygon | Network.MATIC_MAINNET | Network.MATIC_TESTNET |
After change
| Ethereum | Network.ETHEREUM | Network.ROPSTEN |
| Polygon | Network.POLYGON | Network.MUMBAI |
For more details, please see here.
BNB Smart Chain Support
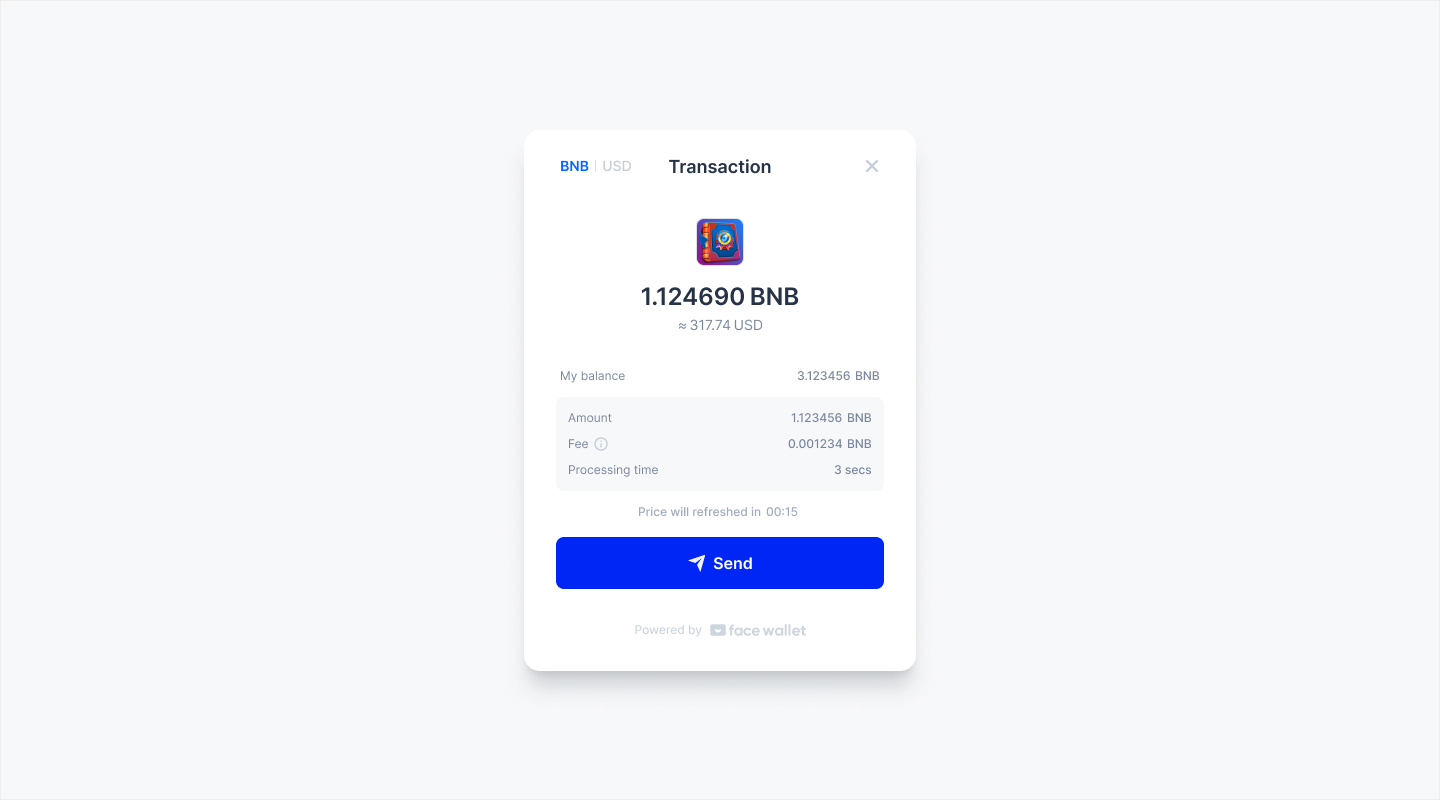
Face Wallet supports BNB Smart Chain!
Now, when you initialize the Face object, you can link the Face Wallet on the BNB Smart Chain by using Network.BINANCE_COIN_MAINNET or Network.BINANCE_COIN_TESTNET as the network parameter.
For more details, please see here.
Klaytn Support
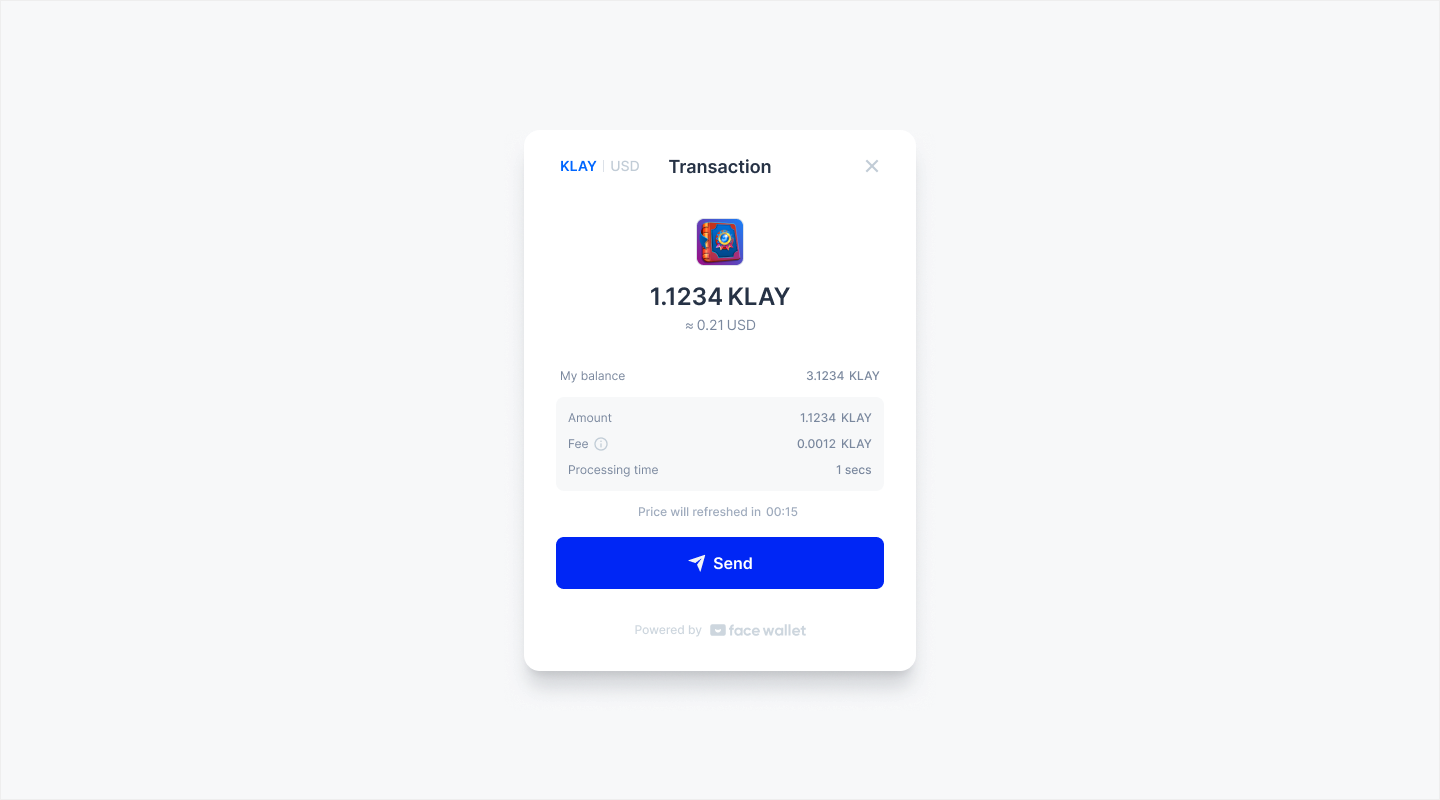
Face Wallet supports Klaytn blockchain network!
Now, when you initialize the Face object, you can link the Face Wallet on Klaytn by using Network.KLAYTN_MAINNET or Network.KLAYTN_TESTNET as the network parameter.
For more details, please see here.
UI support for ERC-1155-type NFT transfer
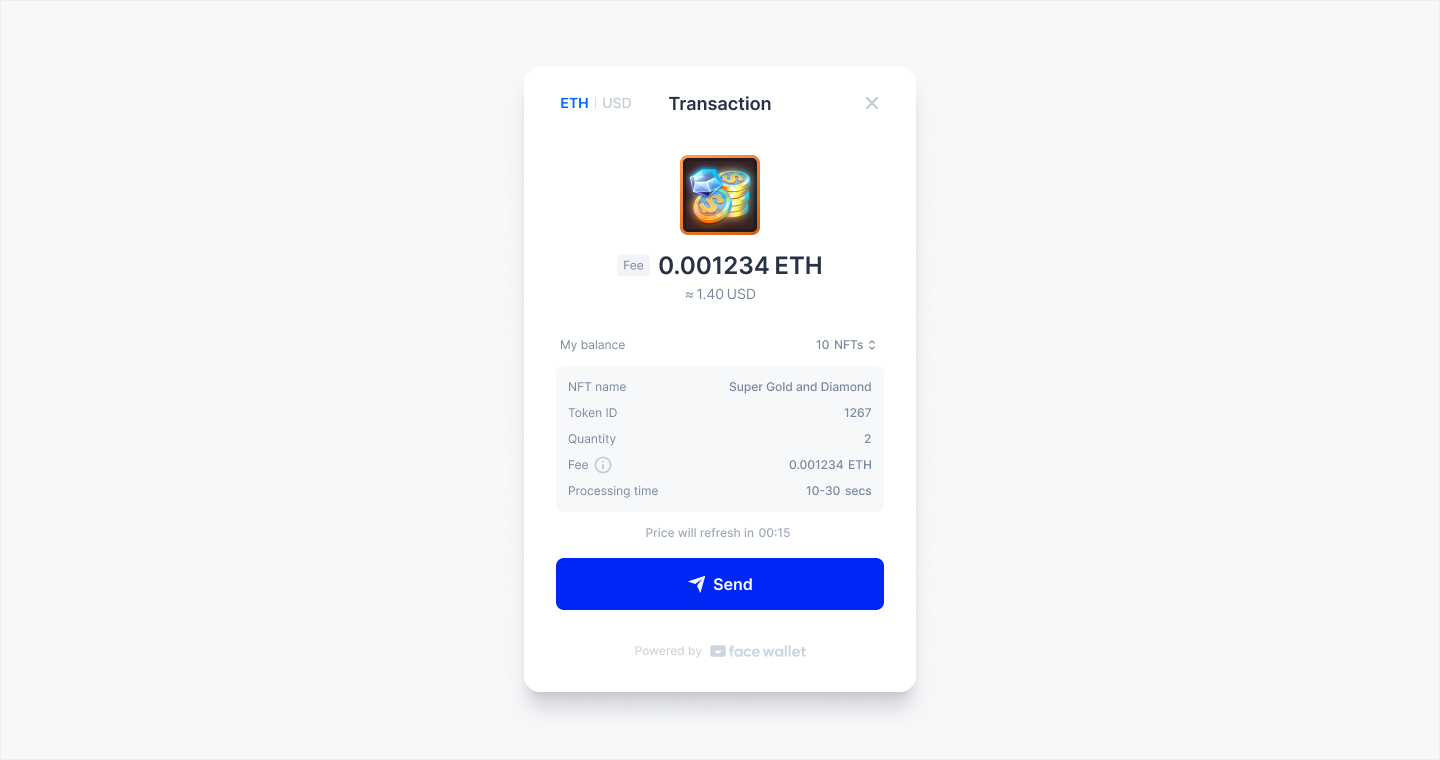
Face Wallet supports the transaction UI for ERC-1155-type NFT transfers.
Users can check the NFT balance, name, image, quantity, etc. for a specific Token ID on the transaction transfer screen.
For more details, please see here.
Sample DApp Example Codes and Demo Page Improvement
To enable you to see how you can use Face Wallet SDK, we have improved the existing Sample DApp example codes and the Demo page.
Integrate the Face Wallet to DApps more effortlessly and quickly through the code of the webpage created with React.
And visit our Demo page to check out and test the features the Face Wallet offers.
For more details, please see here.
Limited SMS verification attempts
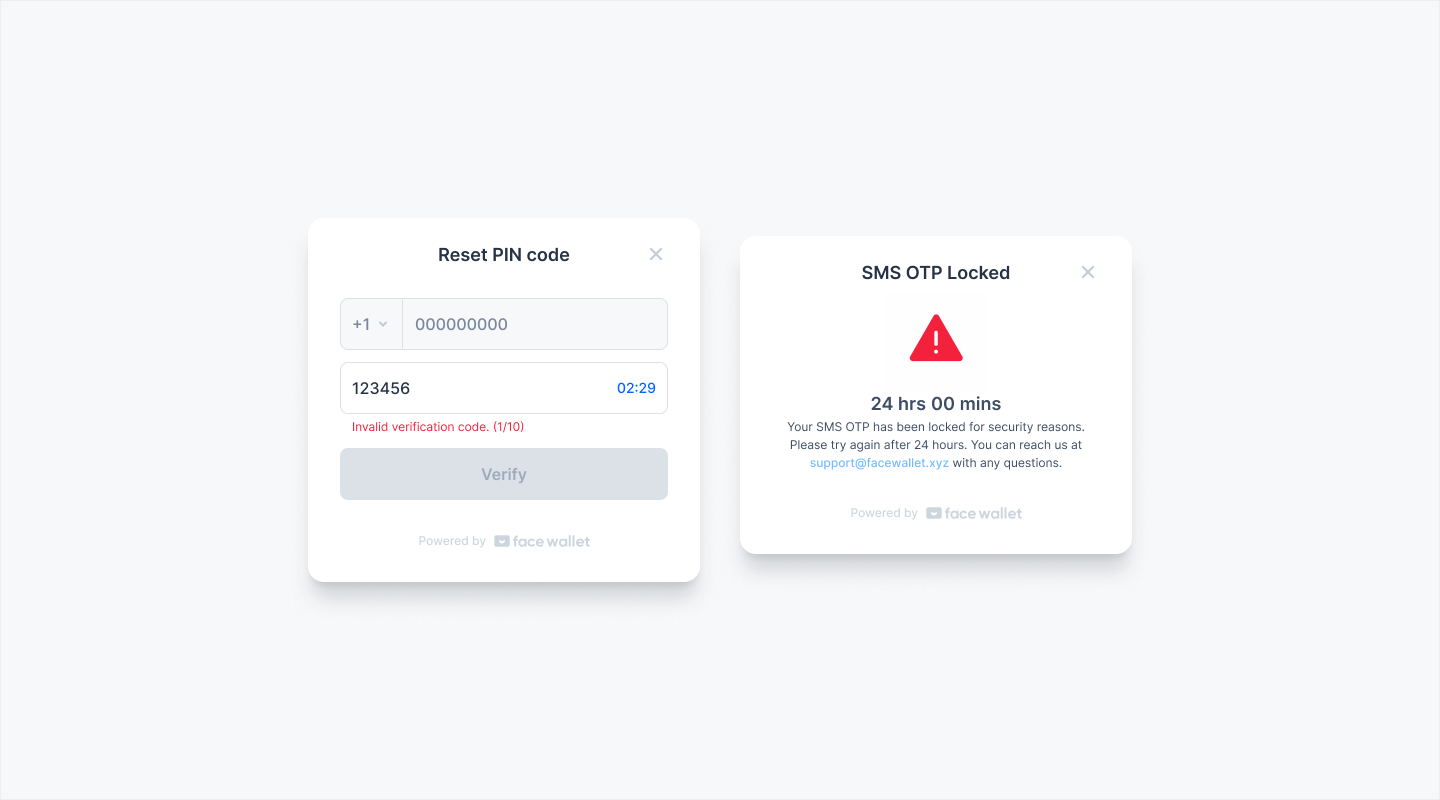
To reset the PIN code, the user must verify via SMS. We improved the system so that if a user enters a wrong SMS verification code 10 times in a row, SMS verification will be blocked for 24 hours. This security safeguard prevents attacks that randomly enter SMS verification codes.